 Lax bring your own device (BYOD) policies are a growing concern for businesses. If not managed properly, these can pose security risks to your organization. How can you mitigate the risks associated with the BYOD trend? Whether your employees are using smartphones, tablets, or laptops, you need a BYOD security policy. Additionally, you need to […]
Lax bring your own device (BYOD) policies are a growing concern for businesses. If not managed properly, these can pose security risks to your organization. How can you mitigate the risks associated with the BYOD trend? Whether your employees are using smartphones, tablets, or laptops, you need a BYOD security policy. Additionally, you need to […]
The post BYOD tips to improve security appeared first on Complete Technology Resources, Inc..
 Lax bring your own device (BYOD) policies are a growing concern for businesses. If not managed properly, these can pose security risks to your organization. How can you mitigate the risks associated with the BYOD trend? Whether your employees are using smartphones, tablets, or laptops, you need a BYOD security policy. Additionally, you need to […]
Lax bring your own device (BYOD) policies are a growing concern for businesses. If not managed properly, these can pose security risks to your organization. How can you mitigate the risks associated with the BYOD trend? Whether your employees are using smartphones, tablets, or laptops, you need a BYOD security policy. Additionally, you need to […]
Lax bring your own device (BYOD) policies are a growing concern for businesses. If not managed properly, these can pose security risks to your organization. How can you mitigate the risks associated with the BYOD trend?
Whether your employees are using smartphones, tablets, or laptops, you need a BYOD security policy. Additionally, you need to be aware of the key BYOD security risks:
- Loss or theft of device – Employees often bring their personal devices wherever they go. This means there’s a higher chance of devices being lost or stolen, and a greater risk of the company data that’s stored or accessed on these being compromised.
- Data loss – In the event that a device is lost, stolen, or damaged, any locally stored data may be lost permanently if it’s not backed up in real time.
- Man-in-the-middle (MITM) attacks – Public Wi-Fi spots are convenient for getting some work done, but they’re also popular hunting grounds for cybercriminals who use MITM to intercept data being transmitted over public networks.
- Jailbroken devices – Jailbreaking is the process of removing the restrictions imposed by the manufacturer of a device, typically to allow the installation of unauthorized or third-party software. This increases the risk of an employee inadvertently installing malicious software on a personal device.
- Security vulnerabilities – Every operating system (and the software that runs on it) has its own unique set of security flaws and vulnerabilities, which means that allowing staff to use any device and operating system increases the risk of a data breach or malware infection.
- Malware – A personal device that has been infected with malware can spread that malware to other devices connected to the company network and cause data loss and downtime.
To mitigate risks, it’s important to devise a BYOD security policy that works for the needs of your business as well as the needs of your employees. Here are some tips:
Make passwords compulsory on all BYOD devices
Prevent unauthorized access to company data by enforcing the use of passwords on all BYOD devices. Passwords should be long and unique.
Create a blacklist of prohibited applications
Blacklisting involves prohibiting the installation of certain applications on BYOD devices that are used for work purposes. This includes applications such as file sharing and social networking apps. The simplest way to blacklist applications is through a mobile device management platform that enables IT administrators to secure and enforce policies on enrolled devices.
Restrict data access
Adopt the principle of least privilege on both BYOD and company devices. This means that a user is able to access only the data and software required to do their job. This can reduce the effects of certain types of malware and limit the fallout in the event of a data breach.
Invest in reliable security solutions for devices
Protect BYOD devices with reputable antivirus software to identify and stop threats before they can make changes to the device. This is vital for protecting mission-critical data and avoiding downtime.
Backing up device data
A well-thought-out BYOD policy can go a long way toward minimizing the risk of a security breach, but if something manages to slip past your defenses, you need a process in place for restoring your data to its former state. Have a comprehensive backup strategy to ensure that any data stored locally on a BYOD device can be quickly recovered.
Educate your staff about security
The vast majority of BYOD-related security risks involve human error. Educate your employees about proper mobile safety. This includes how to spot apps that could contain malware, sharing security threat updates, and teaching them how to secure their devices by going beyond default security settings.
It’s also a great idea to work with an IT partner like us. As experts, we keep tabs on the latest trends and innovations related to BYOD and will recommend solutions that work for your company. Contact us today to see how we can help.
The post BYOD tips to improve security appeared first on Complete Technology Resources, Inc..

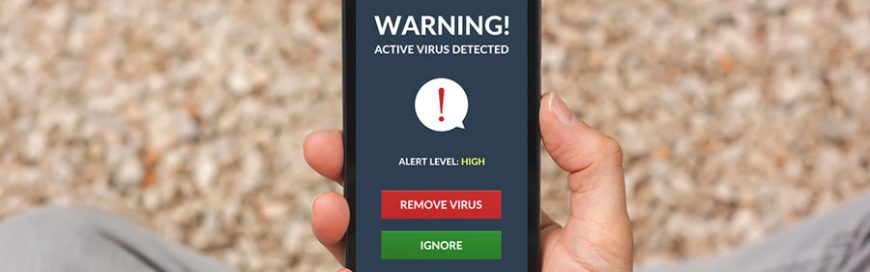 As a smartphone user, you should be just as concerned about your phone’s security from malware as you are about its physical safety. Malware and other forms of cyberthreats are becoming more and more common in smartphones and ignoring them can lead to disaster. Mobile malware MO Mobile malware can be just as harmful to […]
As a smartphone user, you should be just as concerned about your phone’s security from malware as you are about its physical safety. Malware and other forms of cyberthreats are becoming more and more common in smartphones and ignoring them can lead to disaster. Mobile malware MO Mobile malware can be just as harmful to […] Companies — small- and medium-sized businesses, in particular — struggle to protect their data. For one, they make mistakes in the strategies they employ to protect their IT infrastructure. If your organization still does one or more of these bad security practices, act quickly to correct them. Open wireless networks With one main internet line […]
Companies — small- and medium-sized businesses, in particular — struggle to protect their data. For one, they make mistakes in the strategies they employ to protect their IT infrastructure. If your organization still does one or more of these bad security practices, act quickly to correct them. Open wireless networks With one main internet line […]